Cyberbullying

Cyberbullying: A Documentary
A video about what the world has come to due to the inappropriate use of the Internet. By: Olivia Negron, Kara Swenson, and Shani Robinson.
Cyberbullying is the use of Information Technology to harm or harass other people in a deliberate, repeated, and hostile manner. According to U.S. Legal Definitions, Cyber-bullying could be limited to posting rumors or gossips about a person in the internet bringing about hatred in other’s minds; or it may go to the extent of personally identifying victims and publishing materials severely defaming and humiliating them.
With the increase in use of these technologies, cyberbullying has become increasingly common, especially among teenagers. Awareness has also risen, due in part to high profile cases like the Suicide of Tyler Clementi.
Definition – Legal Definition
Cyberbullying is defined in legal glossaries as
- actions that use information and communication technologies to support deliberate, repeated, and hostile behavior by an individual or group, that is intended to harm another or others.
- use of communication technologies for the intention of harming another person
- use of internet service and mobile technologies such as web pages and discussion groups as well as instant messaging or SMS text messaging with the intention of harming another person.
Examples of what constitutes cyberbullying include communications that seek to intimidate, control, manipulate, put down, falsely discredit, or humiliate the recipient. The actions are deliberate, repeated, and hostile behavior intended to harm another. Cyberbullying has been defined by The National Crime Prevention Council: “When the Internet, cell phones or other devices are used to send or post text or images intended to hurt or embarrass another person.”
A cyberbully may be a person whom the target knows or an online stranger. A cyberbully may be anonymous and may solicit involvement of other people online who do not even know the target. This is known as a ‘digital pile-on.’
Cyberbullying vs. Cyberstalking
The practice of cyberbullying is not limited to children and, while the behavior is identified by the same definition when practiced by adults, the distinction in age groups sometimes refers to the abuse as cyberstalking or cyberharassment when perpetrated by adults toward adults. Common tactics used by cyberstalkers are performed in public forums, social media or online information sites and are intended to threaten a victim’s earnings, employment, reputation, or safety. Behaviors may include encouraging others to harass the victim and trying to affect a victim’s online participation. Many cyberstalkers try to damage the reputation of their victim and turn other people against them.
Cyberstalking may include false accusations, monitoring, making threats, identity theft, damage to data or equipment, the solicitation of minors for sex, or gathering information in order to harass. A repeated pattern of such actions and harassment against a target by an adult constitutes cyberstalking. Cyberstalking often features linked patterns of online and offline behavior. There are consequences of law in offline stalking and online stalking, and cyber-stalkers can be put in jail. Cyberstalking is a form of cyberbullying.
Comparison to Traditional Bullying
Certain characteristics inherent in online technologies increase the likelihood that they will be exploited for deviant purposes. Unlike physical bullying, electronic bullies can remain virtually anonymous using temporary email accounts, pseudonyms in chat rooms, instant messaging programs, cell-phone text messaging, and other Internet venues to mask their identity; this perhaps frees them from normative and social constraints on their behavior.
Additionally, electronic forums often lack supervision. While chat hosts regularly observe the dialog in some chat rooms in an effort to police conversations and evict offensive individuals, personal messages sent between users (such as electronic mail or text messages) are viewable only by the sender and the recipient, thereby outside the regulatory reach of such authorities. In addition, when teenagers know more about computers and cellular phones than their parents or guardians, they are therefore able to operate the technologies without concern that a parent will discover their experience with bullying (whether as a victim or offender).
Another factor is the inseparability of a cellular phone from its owner, making that person a perpetual target for victimization. Users often need to keep their phone turned on for legitimate purposes, which provides the opportunity for those with malicious intentions to engage in persistent unwelcome behavior such as harassing telephone calls or threatening and insulting statements via the cellular phone’s text messaging capabilities. Cyberbullying thus penetrates the walls of a home, traditionally a place where victims could seek refuge from other forms of bullying. Compounding this infiltration into the home life of the cyberbully victim is the unique way in which the internet can “create simultaneous sensations of exposure (the whole world is watching) and alienation (no one understands).” For youth who experience shame or self-hatred, this effect is dangerous because it can lead to extreme self isolation.
One possible advantage for victims of cyberbullying over traditional bullying is that they may sometimes be able to avoid it simply by avoiding the site/chat room in question. Email addresses and phone numbers can be changed; in addition, most e-mail accounts now offer services that will automatically filter out messages from certain senders before they even reach the inbox, and phones offer similar caller ID functions.
However, this does not protect against all forms of cyberbullying; publishing of defamatory material about a person on the internet is extremely difficult to prevent and once it is posted, many people or archiving services can potentially download and copy it, at which point it is almost impossible to remove from the Internet. Some perpetrators may post victims’ photos, or victims’ edited photos like defaming captions or pasting victims’ faces on nude bodies. Examples of famous forums for disclosing personal data or photos to “punish” the “enemies” include the Hong Kong Golden Forum, Live Journal, and more recently JuicyCampus. Despite policies that describe cyberbullying as a violation of the terms of service, many social networking Web sites have been used to that end.
Manuals to educate the public, teachers and parents summarize, “Cyberbullying is being cruel to others by sending or posting harmful material using a cell phone or the internet.” Research, legislation and education in the field are ongoing. Basic definitions and guidelines to help recognize and cope with what is regarded as abuse of electronic communications have been identified.
- Cyberbullying involves repeated behavior with intent to harm and repeated nature
- Cyberbullying is perpetrated through Harassment, Cyberstalking, Denigration (sending or posting cruel rumors and falsehoods to damage reputation and friendships), Impersonation, Exclusion (intentionally and cruelly excluding someone from an online group)
Cyberbullying can be as simple as continuing to send e-mails or text messages harassing someone who has said they want no further contact with the sender. It may also include public actions such as repeated threats, sexual remarks, pejorative labels (i.e., hate speech) or defamatory false accusations), ganging up on a victim by making the person the subject of ridicule in online forums, hacking into or vandalizing sites about a person, and posting false statements as fact aimed a discrediting or humiliating a targeted person. Cyberbullying could be limited to posting rumors about a person on the internet with the intention of bringing about hatred in others’ minds or convincing others to dislike or participate in online denigration of a target. It may go to the extent of personally identifying victims of crime and publishing materials severely defaming or humiliating them.
Cyberbullies may disclose victims’ personal data (e.g. real name, home address, or workplace/schools) at websites or forums or may use impersonation, creating fake accounts, comments or sites posing as their target for the purpose of publishing material in their name that defames, discredits or ridicules them. This can leave the cyberbully anonymous which can make it difficult for the offender to be caught or punished for their behavior. Though, not all cyberbullies use anonymity. Text or instant messages and emails between friends can also be cyberbullying if what is said or displayed is hurtful to the participants.
Some cyberbullies may also send threatening and harassing emails, instant messages or texts to the victims. Others post rumors or gossip and instigate others to dislike and gang up on the target.
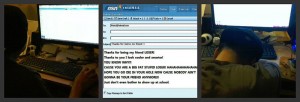 Cyberbullying by email from a fictional friend@hotmail.com
Cyberbullying by email from a fictional friend@hotmail.com
The recent use of mobile applications and rise of smartphones have yielded to a more accessible form of cyberbullying. It is expected that cyberbullying via these platforms will be associated with bullying via mobile phones to a greater extent than exclusively through other more stationary internet platforms. In addition, the combination of cameras and Internet access and the instant availability of these modern smartphone technologies yield themselves to specific types of cyberbullying not found in other platforms. It is likely that those cyberbullied via mobile devices will experience a wider range of cyberbullying types than those exclusively bullied elsewhere.
In Social Media

Cyberbullying can take place on social media sites such as Facebook, Myspace, and Twitter. “By 2008, 93% of young people between the ages of 12 and 17 were online. In fact, youth spend more time with media than any single other activity besides sleeping.” There are many risks attached to social media cites, and cyberbullying is one of the larger risks. One million children were harassed, threatened or subjected to other forms of cyberbullying on Facebook during the past year, while 90% of social media-using teens who have witnessed online cruelty say they have ignored mean behavior on social media, and 35% have done this frequently. 95% of social media-using teens who have witnessed cruel behavior on social networking sites say they have seen others ignoring the mean behavior, and 55% witness this frequently. ”The most recent case of cyber-bullying and illegal activity on Facebook involved a memorial page for the young boys who lost their lives to suicide due to anti-gay bullying. The page quickly turned into a virtual grave desecration and platform condoning gay teen suicide and the murdering of homosexuals. Photos were posted of executed homosexuals, desecrated photos of the boys who died and supposed snuff photos of gays who have been murdered. Along with this were thousands of comments encouraging murder sprees against gays, encouragement of gay teen suicide, death threats etc. In addition, the page continually exhibited pornography to minors.”
PBS This Emotional Life Clip (cyberbullying)
A tribute to Jeff Johnston (R.I.P.) who committed suicide at 15 after relentless bullying by Juju Chang, Linda Owens and Jonann Brady. More info on http://www.pbs.org/thisemotionallife/.
In Gaming
Sexual harassment as a form of Cyberbullying is common in Video game culture. A study by the Journal of Experimental Social Psychology suggests that this harassment is due in part to the portrayal of women in video games. This harassment generally involves slurs directed towards women, sex role stereotyping, and overaggressive language.
In one case, in which Capcom sponsored an internet streamed reality show pitting fighting game experts against each other for a prize of $25,000, one female gamer forfeited a match due to intense harassment. The coach of the opposing team, Aris Bakhtanians, stated, “The sexual harassment is part of the culture. If you remove that from the fighting game community, it’s not the fighting game community… it doesn’t make sense to have that attitude. These things have been established for years.”
A study from National Sun Yat-sen University observed that children who enjoyed violent video games were far more likely to both experience and perpetrate cyberbullying.
Law Enforcement: Cyberbullying, Cyberstalking and Electronic Harassment
A majority of states have laws that explicitly include electronic forms of communication within stalking or harassment laws.
Most law enforcement agencies have cyber-crime units and often Internet stalking is treated with more seriousness than reports of physical stalking. Help and resources can be searched by State or area.
Schools
The safety of schools is increasingly becoming a focus of state legislative action. There was an increase in cyberbullying enacted legislation between 2006–2010. Initiatives and curriclulum requirements also exist in the UK (the Ofsted eSafety guidance) and Australia (Overarching Learning Outcome 13). In 2012, a group of teens in New Haven, Connecticut developed an app to help fight bullying. Called “Back Off Bully” (BOB), the web app is an anonymous resource for computer, smart phone or iPad. When someone witnesses or is the victim of bullying, they can immediately report the incident. The app asks questions about time, location and how the bullying is happening. As well as providing positive action and empowerment over an incident, the reported information helps by going to a data base where administrators study it. Common threads are spotted so others can intervene and break the bully’s pattern. BOB, the brainchild of fourteen teens in a design class, is being considered as standard operating procedure at schools across the state.
Protection for Victims of Any Age
There are laws that only address online harassment of children or focus on child predators as well as laws that protect adult cyberstalking victims, or victims of any age. Currently, there are 45 cyberstalking (and related) laws on the books.
While some sites specialize in laws that protect victims age 18 and under, Working to Halt Online Abuse is a help resource containing a list of current and pending cyberstalking-related United States federal and state laws. It also lists those states that do not have laws yet and related laws from other countries. The Global Cyber Law Database (GCLD) aims to become the most comprehensive and authoritative source of cyber laws for all countries.
Children and Adolescents
Kids report being mean to each other online beginning as young as 2nd grade. According to research, boys initiate mean online activity earlier than girls do. However, by middle school, girls are more likely to engage in cyberbullying than boys. Whether the bully is male or female, his or her purpose is to intentionally embarrass others, harass, intimidate, or make threats online to one another. This bullying occurs via email, text messaging, posts to blogs, and web sites.
The National Crime Prevention Association lists tactics often used by teen cyberbullies.
- Pretend they are other people online to trick others
- Spread lies and rumors about victims
- Trick people into revealing personal information
- Send or forward mean text messages
- Post pictures of victims without their consent
Studies in the psychosocial effects of cyberspace have begun to monitor the impacts cyberbullying may have on the victims, and the consequences it may lead to. Consequences of cyberbullying are multi-faceted, and affect online and offline behavior. Research on adolescents reported that changes in the victims’ behavior as a result of cyberbullying could be positive. Victims “created a cognitive pattern of bullies, which consequently helped them to recognize aggressive people.” However, the Journal of Psychosocial Research on Cyberspace abstract reports critical impacts in almost all of the respondents’, taking the form of lower self-esteem, loneliness, disillusionment, and distrust of people. The more extreme impacts were self-harm. Children have killed each other and committed suicide after having been involved in a cyberbullying incident.
The most current research in the field defines cyberbullying as “an aggressive, intentional act or behaviour that is carried out by a group or an individual repeatedly and over time against a victim who cannot easily defend him or herself” (Smith & Slonje, 2007, p. 249). Though the use of sexual remarks and threats are sometimes present in cyberbullying, it is not the same as sexual harassment, typically occurs among peers, and does not necessarily involve sexual predators.
Some cases of digital self-harm have been reported, where an individual engages in cyberbullying against themselves.
Adults

Stalking online has criminal consequences just as physical stalking. A target’s understanding of why cyberstalking is happening is helpful to remedy and take protective action to restore remedy. Cyberstalking is an extension of physical stalking. Among factors that motivate stalkers are: envy, pathological obsession (professional or sexual), unemployment or failure with own job or life; intention to intimidate and cause others to feel inferior; the stalker is delusional and believes he/she “knows” the target; the stalker wants to instill fear in a person to justify his/her status; belief they can get away with it (anonymity). UK National Workplace Bullying Advice Line theorizes that bullies harass victims in order to make up for inadequacies in their own lives.
The US federal cyberstalking law is designed to prosecute people for using electronic means to repeatedly harass or threaten someone online. There are resources dedicated to assisting adult victims deal with cyberbullies legally and effectively. One of the steps recommended is to record everything and contact police.
http://en.wikipedia.org/wiki/Cyberbullying